Photo from Pexels
Photo from Pexels
Originally Posted On: https://blog.axellio.com/perimeter-defense-ignoring-internal-security-threats
The current threat landscape is constantly changing, and threat actors are finding new and innovative ways to circumvent the current monitoring infrastructure to carry out large-scale attacks. Threats can be anywhere, even inside your internal network. Internal attackers are more prevalent than ever before and are hard to detect once they have infiltrated the network. Therefore, a new approach to security monitoring is needed to look beyond perimeter defense to ensure that the internal network is safe.
Threats are everywhere – even inside your network
Verizon in its recent “2021 Data Breach Investigations Report” identified that almost one-third of all breaches are by internal threat actors. Insider threats are any unapproved or malicious internal use of resources, intentional or unintentional. With 94% of all malware being delivered via email, employee negligence still makes up for the majority of insider threats. Email is a good delivery vehicle for attackers as it allows for a direct installation by users who already have access to critical systems. Only about 18% of breaches are because of stolen credentials.
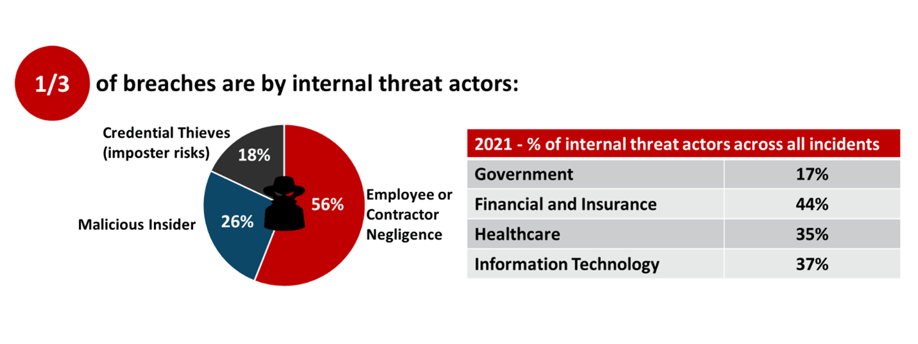 2021 Data Breach Investigations Report, Verizon
2021 Data Breach Investigations Report, Verizon
Once inside, threat actors can hide for weeks or even months, exploring your environment and laying the groundwork for an attack. And with the sophistication and number of attacks ever increasing, it is a question of when, not if, your organization is associated with the next security breach headline.
Beyond perimeter defense
Perimeter defense is still an essential first line against attackers. However, organizations these days have a difficult time defining their perimeter, as the physical network extends into the cloud, the home network of their employees, or even coffee shops and hotels of their road warriors. Jarrod Benson, CISO of Koch Industries, described it the best: “The cloud is the data center, any device is a work device, and the internet is the network”.
And with this increased mobility and exposure, once a device is compromised, threat actors often have free rein, due to the limited segmentation in most networks that would otherwise limit the threat actors’ lateral movements.
Internal traffic still makes up the majority of all traffic, with only a small portion going outside of the network. Unfortunately, perimeter defense tactics only assess a small portion of the total enterprise traffic, leaving most of it unsecured and unmonitored. We must assume that threat actors will penetrate our defenses, so we need to monitor the remaining traffic — at least at strategic points in the network — to better assess the threats internal to our network.
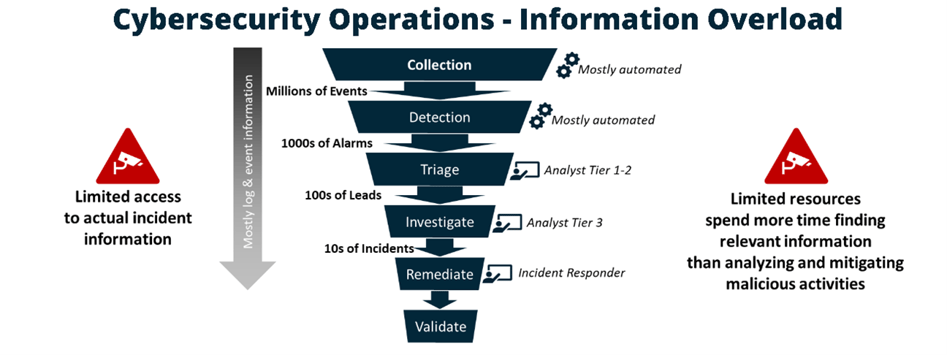
Metadata and tools overload
Most large enterprise organizations receive millions of events per day from their network and security infrastructure. The MITRE ATT&CK® framework identifies 38 data sources essential for tracking the many attack vectors, including process, file, command, and network traffic. Additionally, any of your devices will have many of those processes that need to be monitored.
This means millions of events every day must be cross-correlated and analyzed by each organization. Security information and event management (SIEM) systems have been successfully deployed to reduce this onslaught of events to thousands of alarms per day. These events need to be further analyzed and reduced by security analysts to identify the few incidents that need to be investigated. Unfortunately, few of those are ultimately resolved and remediated. The issue is that besides the volume, none of those events really provide a complete picture of the situation. Each data point is just one piece in the puzzle, and no one knows what the larger picture looks like. Additionally, each analyst is potentially putting together more than one puzzle at any given time. Organizations lack the context to develop the bigger picture.
In addition to data overload, security operations are also overwhelmed with the number of tools they utilize to put this picture together. Palo Alto Networks reported that medium-sized businesses on average use 50 to 60 security tools, versus large organizations, which use as many as 130 security tools on average. This just adds insult to injury, as no single security analyst can effectively utilize that many tools across this ocean of data.
There are way too many logs, events, and alarms that need to be correlated and assessed.
And no single data source is sufficient to build the complete picture on when and how someone got in and who was involved.
Therefore, already resource-strapped SOCs are spending more time trying to find the needle in the haystack than mitigating attacks. The primary challenge for organizations is obtaining and correlating actionable data from across the infrastructure to quickly assess, triage, and mitigate threats. We are very near the tipping point. Actually, we are AT the tipping point!
How to address today’s threats?
There are common misconceptions that IDS/IPS and end-point detection systems block threats at the network boundaries (where are those anyway), and logfiles and network flow information are sufficient to analyze intrusions. Unfortunately, those approaches lead today’s highly reactive and oftentimes overwhelming security operations model. This constant firefighting model leaves organizations vulnerable to insider and persistent threats, and potentially to stolen Intellectual Property (IP) or even ransomware attacks, which LogRhythm outlines in their “Security Operations Maturity Model.”
Organizations need to take a more holistic approach: create more visibility to the internal network traffic to address those resident and internal threats described above, and to get access to data that provides a more comprehensive view of the situation.
With well over two-thirds of your traffic being internal, improving visibility in your internal network appears to be a daunting task, especially with many virtualized applications. Therefore, a careful analysis of your infrastructure and critical applications is needed to prioritize your vulnerable asset lists. With that information, critical links and high-aggregation points can be identified. Using a combination of physical and virtual taps and aggregation of those feeds and using intelligent traffic filtering minimizes the amount of information that needs to be analyzed.
Threat actors take advantage of the shortcomings of meta-data by hiding in legitimate traffic or even modifying the metadata content (e.g., logs) to hide their tracks. This makes threat behavior difficult to detect and even more challenging to respond to. However, capturing network traffic offers immutable evidence that is nearly impossible for hackers to delete or modify. Capturing and analyzing packet data allows for a more complete picture of an attack, enhancing an organization’s threat detection, incident response, and threat prevention. The depth of data available through packets allows your team to provide reliable information about attack patterns across devices, hacker behavior, and the timing of all packets traversing your network.
Axellio – Improving visibility
Axellio Inc. is an innovator in high-performance, 100 Gbps no-loss network traffic capture, distribution, and analysis, and serves network and security operations in commercial enterprise, government, and defense. Axellio’s PacketXpress is an application-agnostic, open platform, combining common, off-the-shelve hardware with APIs to integrate with any commercial and open-source analysis solution – creating a comprehensive and economical security system for network and security operations for better visibility.